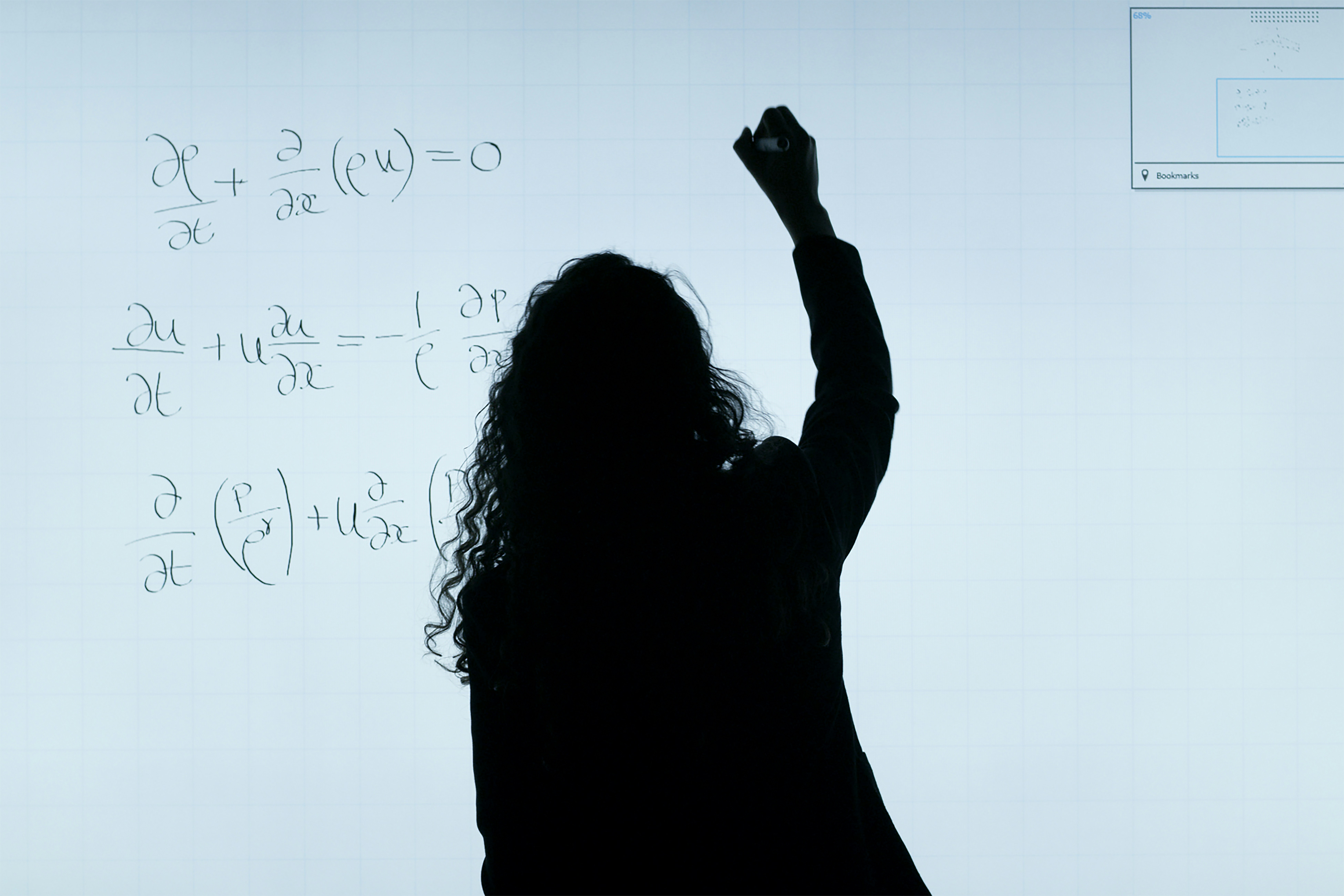Cyber Security Jobs for Career Switchers in Their 30s, 40s & 50s (UK Reality Check)
If you’re thinking about switching into cyber security in your 30s, 40s or 50s, you’re in good company. Across the UK, organisations of all sizes are hiring people from diverse backgrounds to protect systems, data & customers. But with hype around “hackers” & quick-win courses, it’s hard to separate reality from fiction. This guide gives you a UK reality check: which roles genuinely exist, what employers actually want, how training really works, what to expect on salary & progression & whether age matters. Whether you come from finance, project management, operations, law, HR or customer service, there is a credible route into cyber security if you approach it strategically.